How CyDeRinc's Home Cyber-Defense Initiative Works

Since the beginning of Covid and the war in Eastern Europe, cyber attacks on networks in the United States have grown significantly*. The most important thing to know, in defending yourself, is when you are under attack. Do you know when your router/modem is under attack? Do you know if a hacker is working his way through your network, enumerating each device and scanning for vulnerabilities? These things are standard practice for hackers and cyber-criminals. Enterprise networks have monitoring to let them know if this is happening ( they better have good breach insurance if they don't! ) but our home networks remain unguarded. Our home networks need protecting also, to protect those using them.
The Home Cyber-Defense Initiative is CyDeRinc's push to bring cyber awareness and cyber-defense to the modern connected home. With the purchase of a subscription, a networking monitoring device is sent to the user, who easily installs the device.
Currently, CyDeRinc is using Orange Pi Prime SoC boards, a small ARM quad core board with gigabit ethernet and a screen that shows the monitoring is working. From the beginning, the design of the system was meant for people without special IT knowledge. All the subscriber needs to do is plug in the power, and plug in the ethernet. The board will power up, check the internet status and begin listening for bots, malware, viruses, and hackers that are trying to infect devices on your network.
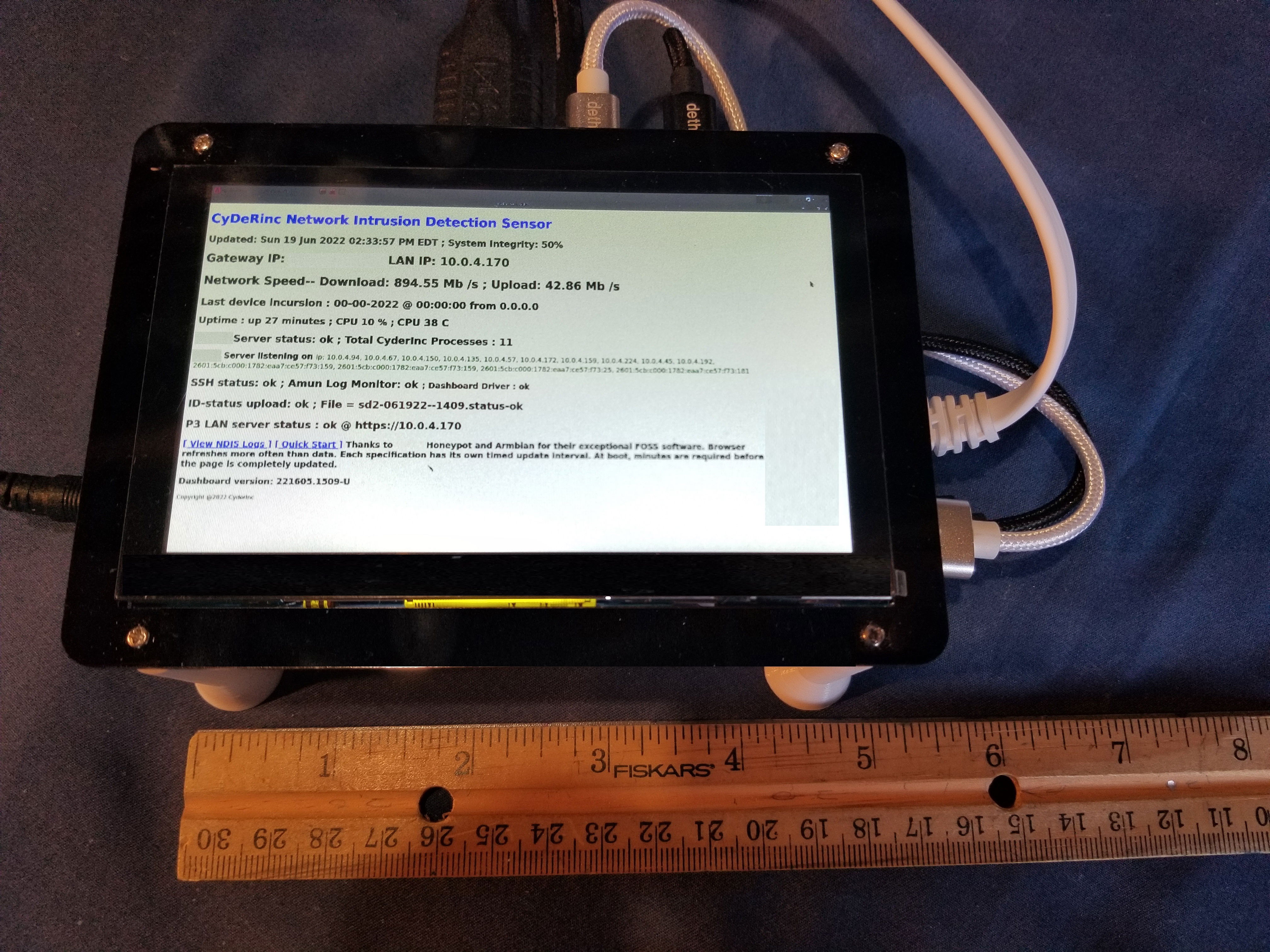
The above device shows an assembled CyderInc Network Intrusion Detection System based on the Orange Pi Prime: the ARM board is mounted on a 3d printed stand that also connects to the screen. Cables connect the screen to the Pi. Power and ethernet cables are all it takes to get the NIDS up and running.
Network incursions happen when a hacker or a bot bypasses a router and scans, enumerates and evaluates all the connected devices for vulnerabilities. However, network incursions, can also be other infected devices on the local subscriber's network, maybe a phone or laptop that was infected connecting to free wifi at a hotel or restaurant. Both incursions are a big cause for concern...
Attacks from within your own network:
Attacks can come from inside your own network. These attacks happen if a device has already been infected with malware. This can happen if a phone or laptop connected to unsecured wifi at a hotel or restaurant. It can happen if you visit a website that has been infected, then that website can pass the virus on to you just by visiting the site. Though many improvements have been made to help prevent this, there are still vulnerabilities being found that enable this type of attack to continue being used.
Attacks from outside your own network:
A few years ago, CyderInc ran a test. We wanted to know just how many attempts were actually being made to breach devices connected to the internet. So we placed an intentionally vulnerable device ( called a honeypot ) on the unprotected internet. What happened? After 12 hours, there were more than 4,000 attempts made to gain control of the device. It happened slowly, but once one bot found it, the IP address was passed around and it eventually became a bot-swarm: many bots attempting to overtake the device, each trying different attacks.
Any router should be able to fend off these types of attacks before a bot-swarm even gets started. But residential routers/modems are the worst secured devices on the internet. They rarely get their firmware updated, and it takes IT network knowledge to set them up securely. By-the-way, I hope your router doesn't still have the default password. These are easily looked up and make your router an easy target.
How we help:
With our custom Network Intrusion Detection Sensor, if something is scanning your network, we (and you ) will know within a few minutes. When the NIDS boots, it assigns itself 13 more IP addresses than the one it is assigned by your router (10 x IPv4, 3 x IPv6). This means it looks like it is 13 devices and not just one on the network, giving itself more attack vectors. If one, or all of these IP addresses are "scanned", a red Incursion alert shows on the screen, and data is uploaded to CyderInc for analysis. Once we look at the data, we will notify you where the incursion came from, and how best to fix the problem.
In this way, a consultant at CyDeRinc will then provide the subscriber with help and guidance in either fixing their router, adding defenses, or disinfecting the local device that caused the alarm. This is the key to the service, helping fix the problem.
Benefits:
Network Connectivity: The device helps monitor the status of your internet connection. It shows IP text in green when your connection is working and red if it drops out. It gives you network information, like external IP, internal IP and status of the system. The device monitors your download and upload speeds to make sure you're getting what you pay for from your internet service provider. It also has links so you can view the information that is sent to CyderInc, so you see exactly what we see. And you don't need the device's small screen to view the information: from any browser in your network, you can view the dashboard and check the status--using the supplied username and password of course! A screenless (headless) version also exists for corporate and enterprise networks.
Home Network Security: We're here to help when a bot or attacker infiltrates your home network. Most people will never know when their network devices are being scanned by a hacker in a foreign, at-war country. One wrong setting in your router, and all your online devices are open to scans and infiltration attempts.
Environment: At CyderInc, we use previously used devices to monitor networks. All devices are wiped clean then operating systems reinstalled. Then we check to make sure there are no connections to unwanted servers from the devices. Some of our boards don't even have built in storage and changing the entire system is as easy as changing an SD card. By using previously-used tech, we help keep our e-waste to a minimum, benefiting the environment. By using low-power devices, we help keep energy costs down. Our systems do not require the latest processors or huge amounts of memory to run, making previously-used tech a great win/win/win for our customers, the environment and CyDeRinc.
Cost: Our goal is to make cyber-defense affordable for users. It's a vast & undefended network of targets on the home front. If you want to know if you are being targeted, you need our service. Our research has shown, that an unprotected device can get more than 4000 attacks in 12 hours! Do you know if your router is protecting your devices?
The NIDS devices that are sent CAN NOT be used for general purpose computing or browsing the internet. Attempting to use them for anything besides network intrusion detection will diminish their capacity for intrusion detection and compromise the entire system of programs that run the defense. These low powered devices are not built for high speed graphical processing. Don't compromise the device using it for something it is not intended to do.
Are you a high net-worth individual or family, a government official, or a business executive that needs a higher level cyber protection? Click our Platinum service below.
Are you responsible for an enterprise network and would like to use this service? Follow the enterprise link below for more options.
If you need a wifi enabled device, make sure to click that option below as well. Using the wifi option provides a little less protection and may slow your wifi speeds when an attack is commencing. But you know as well as I, that it's still better than not knowing when you're being attacked. And the wifi-device option still gives you the same availability of a consultant to assist you in case of an attack.
Purchase a one or two year subscription and begin protecting your home network!
Ethernet cabled device, 1 year:
https://checkout.square.site/merchant/9YTKF1RXDN3HN/checkout/H5GBSXXHOPR4XVPZPNN5HML3
Ethernet cabled device, 2 year:
https://checkout.square.site/merchant/9YTKF1RXDN3HN/checkout/OEBWR4KNLG25JUYWKDOJJOOR
For high-value target people ( government, executives, trade-secrets, net-worth )
Adds extra monitoring of internet traffic:
https://checkout.square.site/merchant/9YTKF1RXDN3HN/checkout/ZMOTWFKIQQBMZ2RLHOVUELGJ
Wifi Enabled device, 2 year:
https://checkout.square.site/merchant/9YTKF1RXDN3HN/checkout/6UQRXQ5JJJ23HZQFQXT7ALRO
Developers/IT Specialist to contribute to project, 1 year:
https://checkout.square.site/merchant/9YTKF1RXDN3HN/checkout/TKEEYRTP2225QVYNF5SMPQNZ
*References:


